In today’s ever-evolving digital landscape, safeguarding online assets is paramount. As a proactive guardian of my website’s security and accessibility, I embarked on a journey to fortify my online presence using Cloudflare Zero Trust—a paradigm shift from the conventional approach of exposing ports.
Embracing Cloudflare Zero Trust
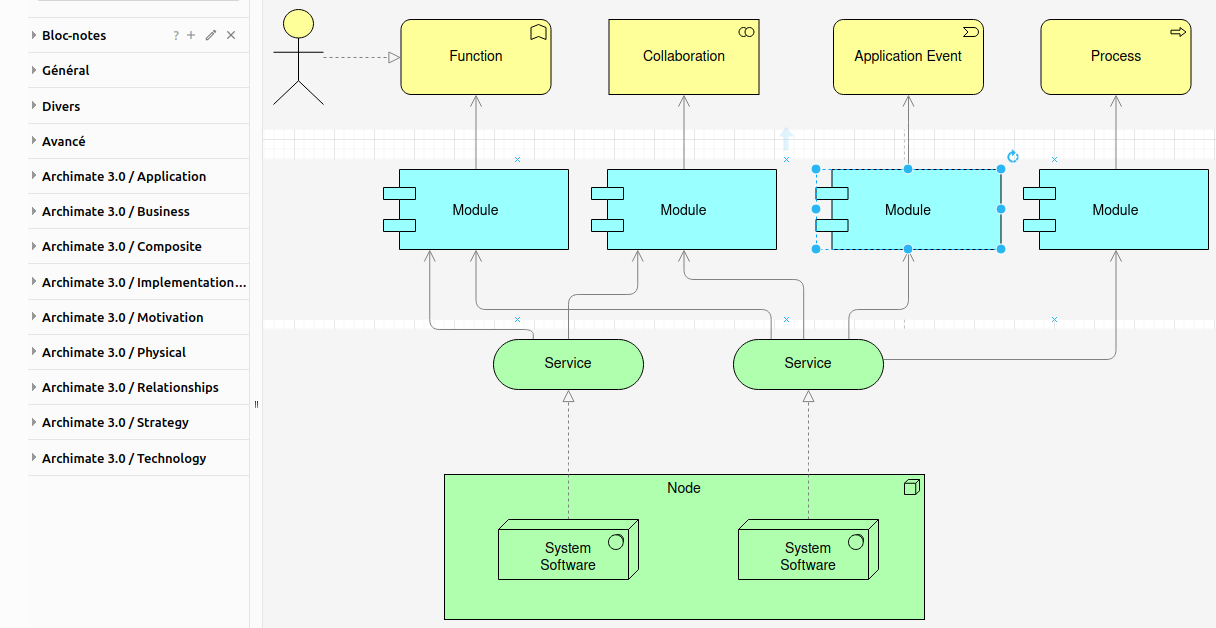
Traditionally, exposing ports on a server left potential vulnerabilities open to cyber threats. Cloudflare Zero Trust, however, presented an innovative alternative. It allowed me to fortify my services by restricting access and enforcing strict authentication measures before granting entry, safeguarding not just my blog but all critical functionalities.
View More: Setting Up Cloudflare Zero Trust
The setup process involved routing all incoming traffic through Cloudflare’s global network. This not only optimized performance but also acted as a shield against DDoS attacks, ensuring a seamless user experience while maintaining robust security measures. Configuring rules within Cloudflare Access provided a granular level of control, defining who could access specific services and from where.
The Essence of Zero Trust: Authentication and Control
At the core of Zero Trust lies the philosophy of verifying every request, irrespective of its origin. Leveraging Multi-Factor Authentication (MFA) and stringent identity verification protocols through Cloudflare Access, I established a secure gateway. This ensured that only authorized users gained access, automatically blocking potential threats and reducing the risk landscape significantly.
View More: Zero Trust Principles in Action
Implementing Zero Trust principles shifted the paradigm from perimeter-based security to an identity-based model. The elimination of direct server access drastically reduced the attack surface, mitigating risks associated with exposed ports. Cloudflare’s real-time threat intelligence continuously updated security protocols, providing a robust defense against emerging threats.
Granular Control and Streamlined Management
The granularity of control provided by Cloudflare’s Zero Trust architecture was transformational. Through an intuitive dashboard, I could fine-tune access permissions in real-time, granting or revoking privileges effortlessly. This not only fortified my security stance but also streamlined management, allowing me to focus on other critical aspects of my website and services.
View More: Simplified Access Management
Cloudflare’s analytics and reporting tools offered comprehensive insights into access attempts, facilitating thorough monitoring and auditing of access patterns. This visibility empowered the prompt detection of anomalies, enabling proactive measures to further enhance security.
Conclusion: A Secure and Accessible Future
In conclusion, adopting Cloudflare Zero Trust to expose my website and services to the internet was a strategic decision that significantly bolstered my security while simplifying access management. The stringent authentication measures, reduced attack surface, real-time threat intelligence, and granular control collectively fortified my online presence. With Cloudflare Zero Trust, I struck a fine balance between accessibility and security, creating a safer, resilient, and future-ready digital environment for my website and services.


Post Comment